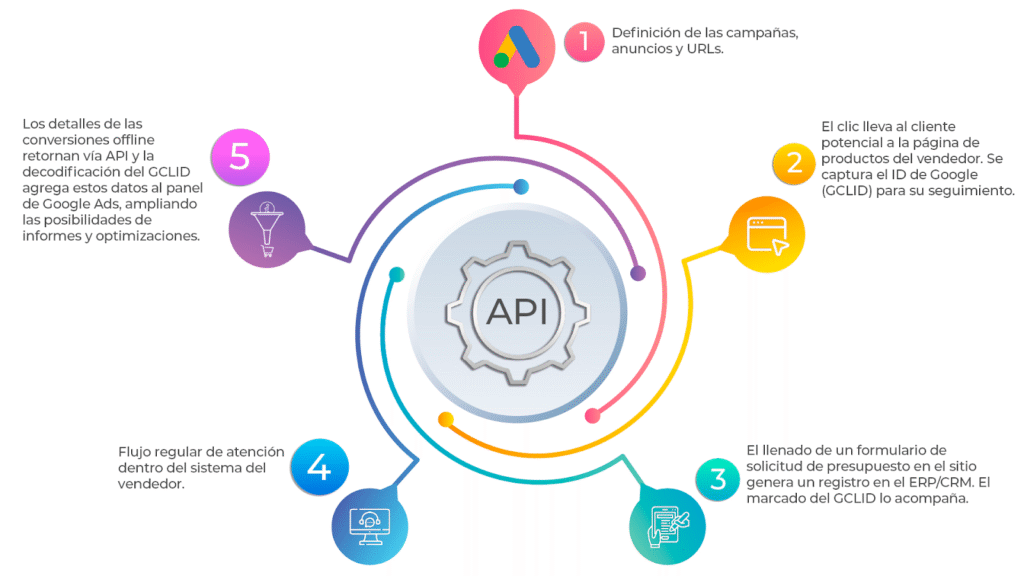
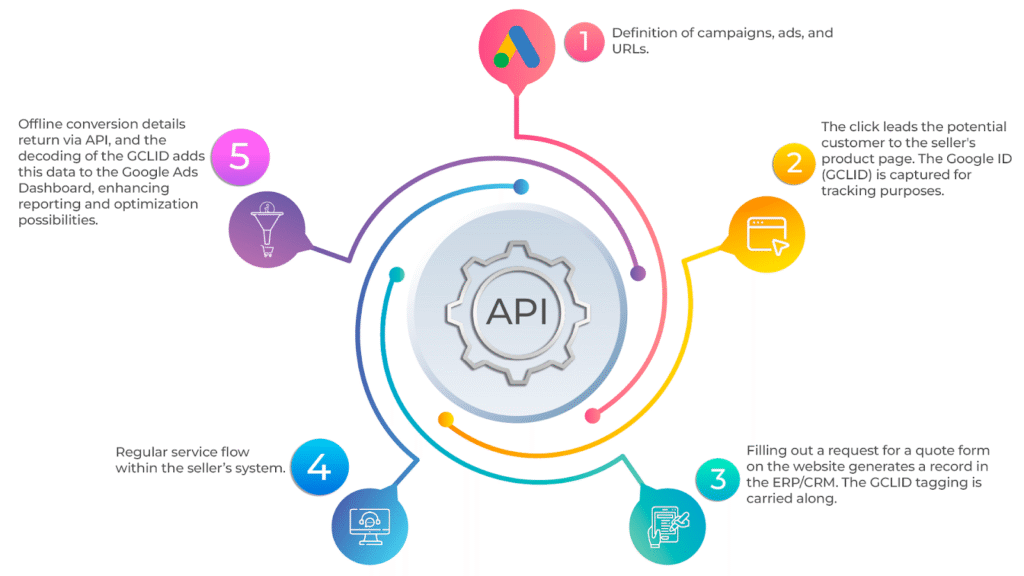
Data Analysis
Authoring and LMS
Collaboration and Design
Low-code development, solutions and integrations via APIs
DevSecOps
Project Management and ITSM
Infrastructure and Cybersecurity
Engineering & GIS

Software Licensing and Umbrella Contract